Key Takeaways
- The White House urges use of memory-safe languages like Rust to reduce security vulnerabilities in code.
- Older lower-level languages like C pose risks of buggy code leading to security incidents.
- Memory-safe languages like Rust offer automatic memory management and error prevention features.
A US government agency has decreed that programmers should favor memory-safe languages like Rust and Java. But why are they better and does this really matter?
What Is the White House Saying?
In a statement on 26 February, the White House Office of the National Cyber Director (ONCD) urged software developers to adopt memory-safe programming languages, like Rust.
We, as a nation, have the ability – and the responsibility – to reduce the attack surface in cyberspace and prevent entire classes of security bugs from entering the digital ecosystem but that means we need to tackle the hard problem of moving to memory safe programming languages.
Why Is It Important?
The ONCD, established in 2021, reports directly to the President, advising them on cybersecurity and related issues. US policy is likely to have a ripple effect across the world of technology.
Many of the worst-ever security vulnerabilities had problems with memory safety as their root cause. Older lower-level languages give programmers a lot of power, but this increases the risk of buggy code causing serious repercussions.
Regardless, usage of memory-safe languages—like Rust, Python, and JavaScript—has long been on the increase. The ONCD is likely making this announcement because less-safe languages like C have been around so long that their legacy code is now ingrained in infrastructure and much of the software we use daily.
What Does an Unsafe Language Look Like?
Unsafe code doesn’t always look scary or even complicated. Take this example of a simple C program:
#include <stdio.h>int main (void) {
int arr[3] = { 0, 0, 0 };
printf("%dn", arr[3]);
return 0;
}
This is a classic example of a bug that can lead to a buffer overflow attack. The programmer has forgotten that arrays in C (and most other languages) are zero-indexed, meaning the first element is at arr[0], etc. Attempting to access arr[3] is therefore a mistake, but one that C will allow:
The value at arr[3] is a valid memory address, like any other, it just doesn’t belong to the array. Any value could be stored there, and the consequences of accessing it or writing to it can range from a program crash to a catastrophic security incident. Many hackers throughout history have exploited such bugs.
Although the C compiler still produces a warning, it also generates an executable. A programmer is free to ignore warnings, and even hide them using compiler flags. C will still let you shoot yourself in the foot while languages like Rust won’t offer you a gun at all.
What Does Memory-Safe Code Look Like?
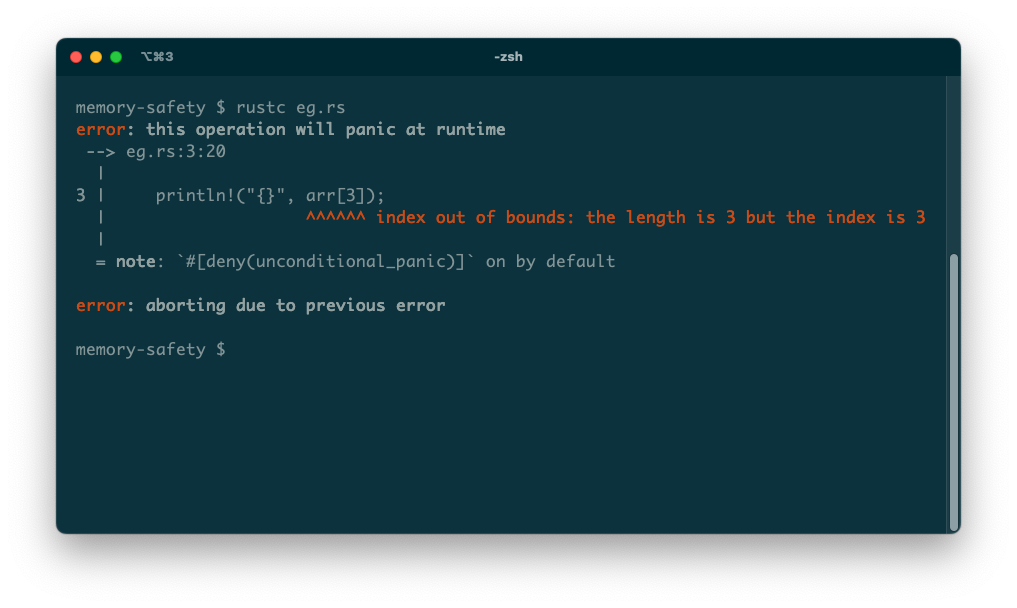
In a memory-safe language like Rust, the same problem simply doesn’t exist. Here’s the same program, in Rust:
fn main() {
let arr: [u32; 5] = [0;3];
println!("{}", arr[3]);
} While this code is syntactically valid, Rust will fail to compile it:
The compiler explains the problem and refuses to produce an executable. Rust simply will not let you run this code.
Rust has many more features besides this, to help protect you. It includes features like smart pointers to handle memory management automatically and prevent null pointer dereferencing.
Should I Switch Languages?
Every programming language has a purpose, so you should be wary of advice to absolutely avoid any, even if it comes from the President. While you may choose to specialize in a particular language, it’s always useful to learn a variety, to expand your options.
Memory safety is a feature of so many modern languages, that you might as well be familiar with at least one. C has its uses, but there are safer options that will cause fewer mishaps. In particular, if you’re looking for an efficient language that has some good safety nets, Rust is a must.